Phishing campaign targets Office users
Microsoft Office 365
Anyone who uses Office 365 could currently be the target of a phishing campaign. Accounts with active 2FA are also targets of the attacks. This is how the attackers act.
news
![]()

In a large-scale phishing campaign, attackers currently want to take over Office accounts. This is what Microsoft security researchers found out. in one blog post the company warns that since September 2021, more than 10,000 organizations have been targeted by the attackers.
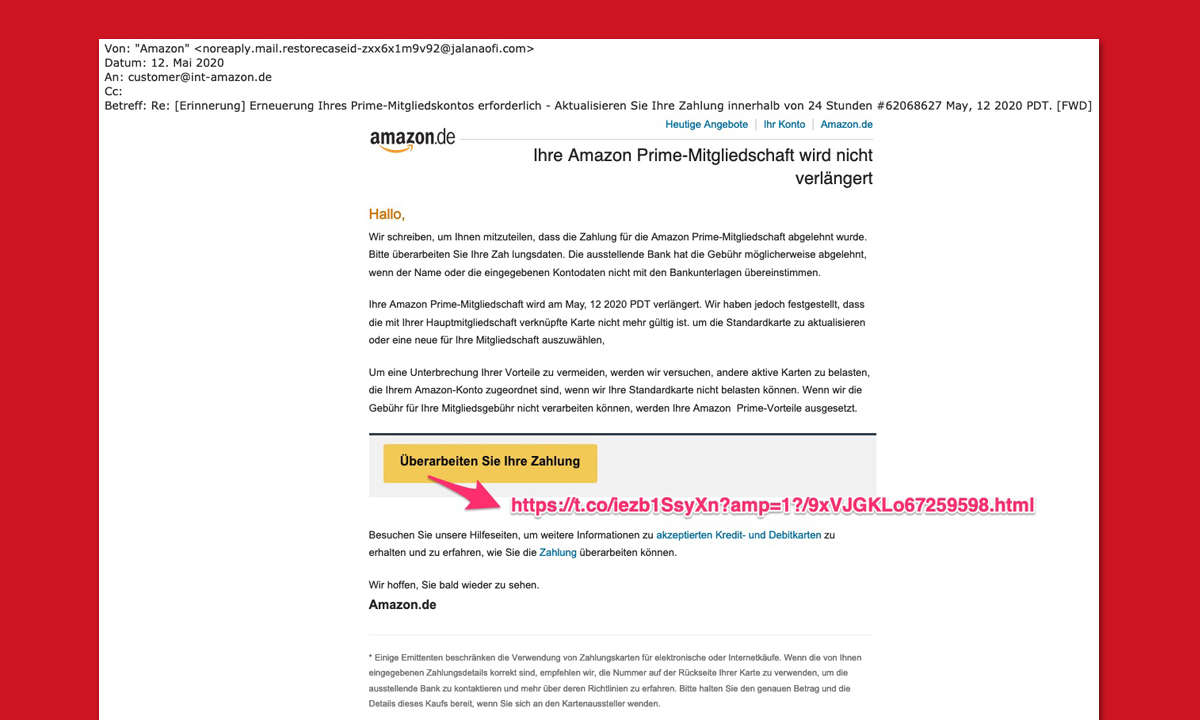
The attackers first send phishing emails with defective links to companies. The email contains an HTML file, for example, which is supposed to hide a voice message for the victim. After the click, the information appears that the voice message is being downloaded. After that, the target is redirected to a supposed Microsoft login page to enter their account details.
In fact, it is an Adversary-in-the-middle (AiTM) website. This sits between two network components, usually client and server, in order to intercept data, in this case login data and session cookies.
The victims’ mail accounts are then taken over with the login data, while the session cookies are used to bypass 2-factor authentication (2FA). After account takeover, the attackers begin a business email compromise (BEC) campaign. So they send fake corporate emails to other targets to get them to transfer payments.
According to Microsoft, phishing attacks are still the most common type of digital attack against companies. Phishing attacks have increased sharply since 2020. In addition, attackers are increasingly preparing to bypass 2FA.
In order to actively protect yourself against the phishing campaign, Microsoft gives a number of instructions:
- Enable Conditional Access policies: Conditional Access policies are evaluated each time an attacker attempts to use a stolen session cookie. Organizations can protect against attacks using stolen credentials by enabling policies such as compliant devices or trusted IP addresses.
- Invest in modern anti-phishing solutions: These monitor and scan incoming emails and visited websites. For example, organizations can deploy web browsers that automatically detect and block malicious websites, including those used in this phishing campaign.
- Continuously check for suspicious or anomalous activity: This does not include looking for login attempts with suspicious characteristics (e.g. location, ISP, user agent, use of anonymization services) or unusual mailbox activities such as creating inbox rules with suspicious purposes or unusual amounts of mail item hits by trusted IP addresses or devices.
Continue to home page
Reference-www.pc-magazin.de